Azure AD Authentication Using SAML
Before You Start
You'll need Azure rights to configure a new Azure AD app.
Create the Azure AD App for Catalog
-
Go to the Azure admin portal at https://aad.portal.azure.com/.
-
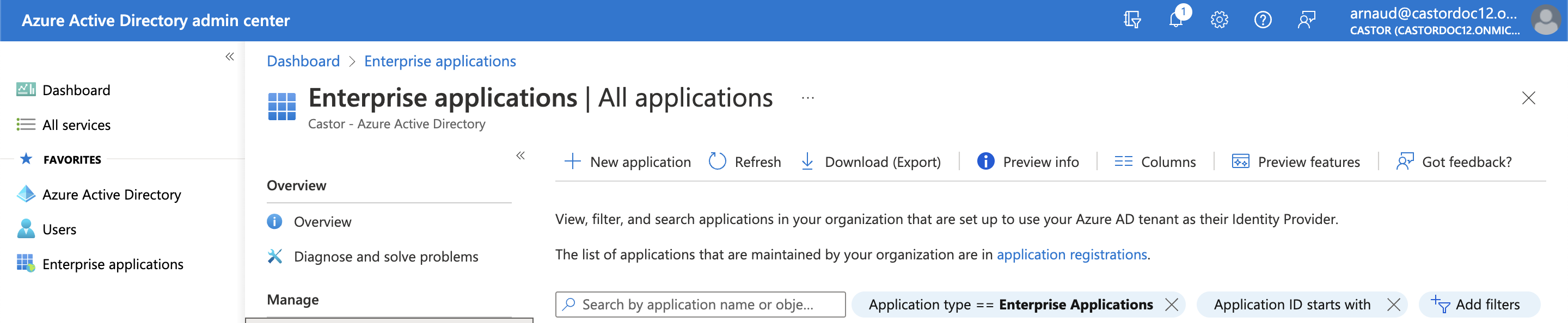
Go to Enterprise applications > All applications.
-
Click New Application.
-
Name your app. For example, Catalog.
-
Select Integrate any other application you don't find in the gallery (Non-gallery).
-
Set the entity ID (identifier) to
production-castorSAML. -
Set the Reply URL based on your account region:
- For accounts using
app.castordoc.com:https://api.castordoc.com/auth/saml/callback - For accounts using
app.us.castordoc.com:https://api.us.castordoc.com/auth/saml/callback
- For accounts using
-
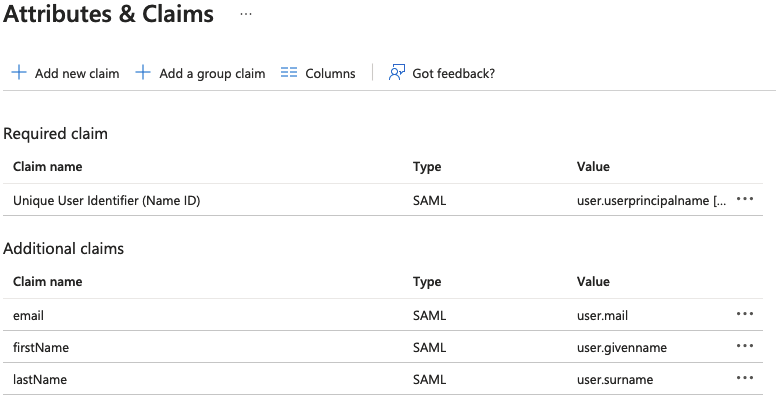
Update the claims with the following mappings.
user.givennamemaps tofirstNameuser.surnamemaps tolastNameuser.mailmaps toemail
danger- Keep the Namespace empty for each claim.
- Claim names are case sensitive.
-
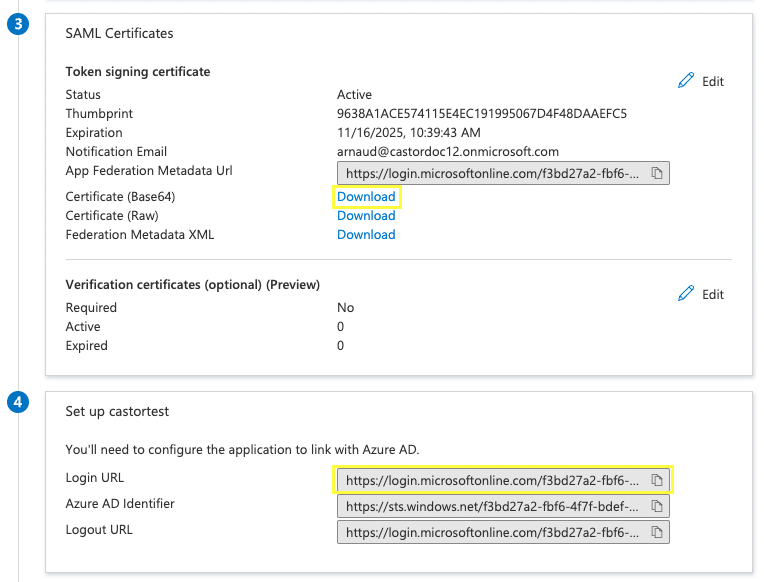
Download the certificate.
Add URL And Certificate to Catalog
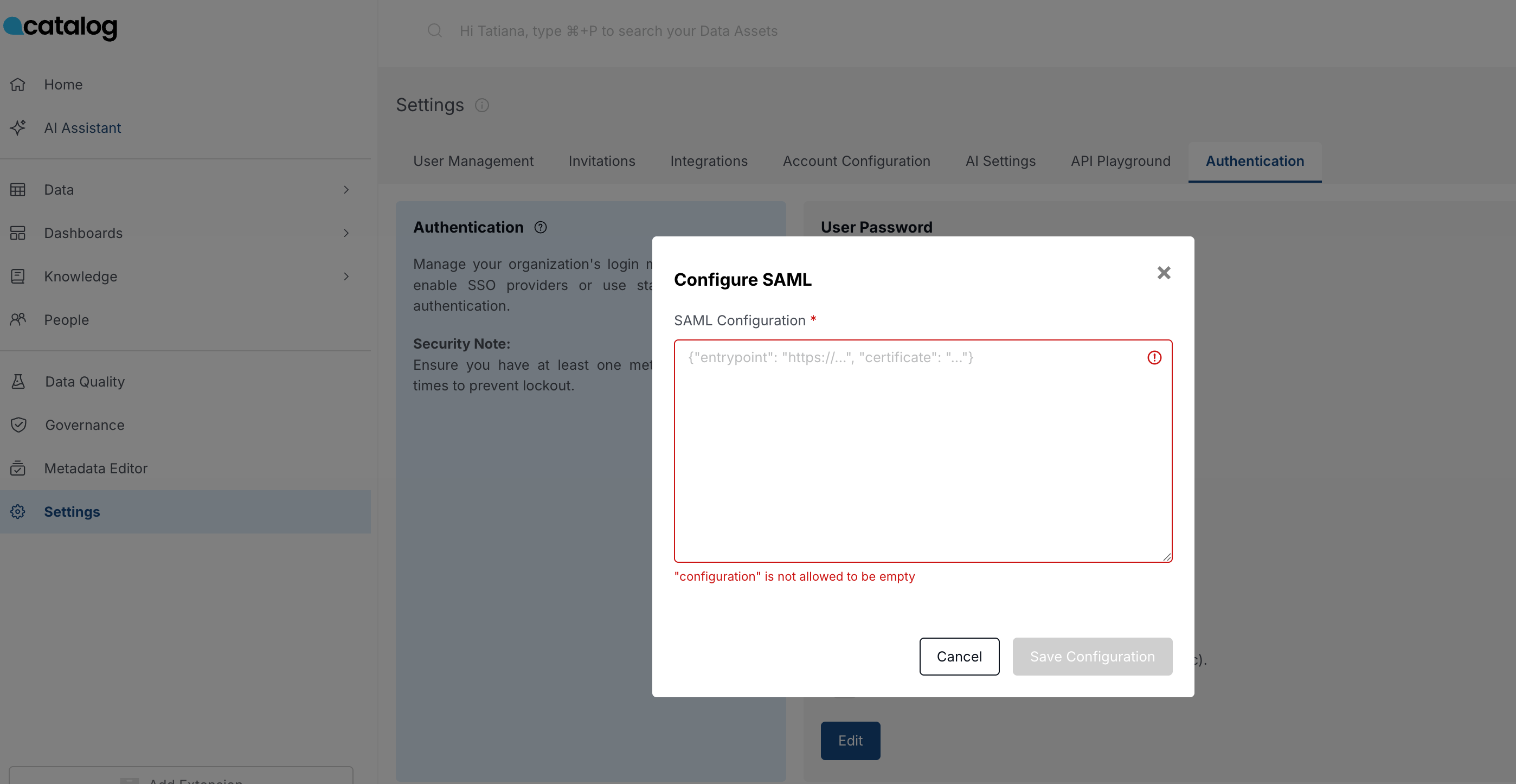
- In Catalog, go to Settings > Authentication.
- Copy and paste the certificate and URL, making sure to format them correctly.
{
"entrypoint": "https://...",
"certificate": "..."
}
Allow Users To Connect To the Catalog App
Make sure to have the right audience allowed to connect to Catalog.
- Go to the admin portal and open the newly created Catalog application.
- Click Users and Groups.
- Add relevant groups and users to give them access to Catalog.
Multiple Authentication Options
Catalog can keep both SAML and email with password strategies active.